Businesses and organizations look to protect their visitors and mitigate risks through both physical security and safety systems. Learn about best practices for designing and maintaining physical security and safety systems in ways that help to protect people and valuable assets from external threats as well as better lower and manage risk.
What we’ll cover in this article:
- What are physical security and safety systems?
- How are these systems different from cybersecurity, and how are they connected?
- Components of physical security
- Examples in various industries
- Strategies for designing and maintaining effective physical security and safety systems that mitigate risk
Let’s get started!
What Are Physical Security and Safety Systems?
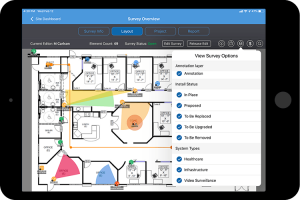
Physical security and safety systems are any material or technological implementations in a physical space that have as their core purpose the safety of people or property or the security of the same.
Examples include video surveillance systems and surveillance cameras, physical security measures, access control systems, and any other security measure that organizations use as part of a security system.
Most organizations in the public and private sectors do not use just one form of physical security. They use a mix of approaches, from security guards and other human personnel to technologies like those listed above.
Physical security and safety systems can help to mitigate numerous potential risks, including loss prevention in retail and other settings and physical access control to manage access to sensitive areas and prevent unauthorized access (including residential facilities on university campuses and restricted access areas on corporate campuses).
How Physical Security Differs from Cyber Security (and How They’re Connected)
Physical security and safety systems are distinct from cybersecurity mitigation efforts, though the two are connected. The latter involves the protection of confidential information, digital assets, and critical infrastructure from cyber criminals and digital threat actors with malicious intent.
Many of the potential threats are digital in nature and don’t involve a physical attack but one of social engineering, where personnel are fooled into giving out sensitive information. These are information security threats, not physical ones.
But some threats bridge the gap between the physical and the digital. Certain directed digital attacks may require physical access to critical assets in restricted areas, such as a server room. Also, many physical security systems include cloud-based and IP addressable endpoints (cloud-connected security cameras, for example). These must be protected digitally just like any other IT asset — and they must be protected from physical security threats just like any other physical asset.
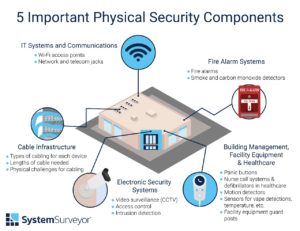
Physical security systems have numerous components, which generally break down into the following categories in terms of system design for smart buildings.
1. Electronic Security Systems
Electronic security systems include:
- Video surveillance systems (CCTV)
- Access control systems
- Intrusion detection
2. Cable Infrastructure
Most electronic physical security devices carry some cabling needs. Cable infrastructure is thus a vital element of any physical security system design. Consider these elements:
- What kinds of cabling are necessary for each device, and where do those cables route to?
- What lengths of cables are necessary for an installation?
- What physical or structural complications exist that create challenges or hindrances to cabling?
3. IT Systems and Communications
Your physical security systems require IT and communications infrastructure as well, including in many cases:
- Wi-Fi access points
- Network and telecom jacks
4. Fire Alarm Systems
Fire alarms, smoke detectors, carbon monoxide detectors, and sprinkler systems are also often considered part of security and safety systems.
5. Building Management, Facility Equipment, Healthcare and More
Last, there are a wide range of industry- and use case-specific technologies that may be a part of your organization’s physical and safety systems. Here are a handful across several industries:
- Panic buttons
- Nurse call systems and defibrillators in healthcare settings
- Motion detectors
- Sensors for vape detections, water sensors, temperature sensors and many others
- Facility equipment guard posts
When planning, executing, or mapping out your organization or campus physical security and safety plans, security teams should be sure to consider all of these categories when conducting a vulnerability assessment — and don’t forget the AV and IT resources that may be in the mix as well.
Examples of Physical Security Risks in Various Industries
One of the complexities that systems integrators must grapple with is the wide variance in needs and risks depending on the nature of the client organization and their business operations. For example, education, healthcare, and government customers all have unique and varying needs, and none of them look like the average corporate campus client.
Additionally, no large campus or organization is monolithic, with unified and uniform security needs in every sector. There will always be variation, with a mix of more- and less-secure areas throughout a campus. Different areas will have different risks as well as risk tolerances (not to mention budgets), and so planning must always be customized according to audience and use cases.
We’ll give just a few examples of how this variation in needs shows up across industries and market segments.
Education (K-12 and University)
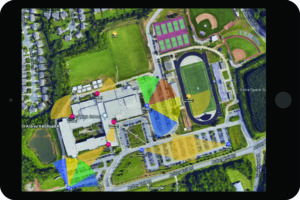
First, consider the education market, which has its share of unique attributes. Universities tend to require longer lead times to accommodate their highly seasonal budget planning and revenue model. They also tend to have specific installation requirements, such as only installing during summer or other breaks, and they may rely on student labor in ways that can affect security planning.
Educational environments (including university and K-12) also have unique concerns related to student safety, whether from physical threats, natural disasters, incidences of violence, or even terrorist attacks. Of course, every campus cares about the safety of its occupants, but the risk assessment tends to look different in an office complex than a university campus.
Retail

Retail environments tend to be primarily concerned with loss prevention, with heavier investments in security cameras, alarms, and (in some cases) physical barriers or traffic control measures. Larger settings such as indoor or outdoor malls also tend to be concerned with physical safety in parking lots and common spaces, as well as prevention of vandalism or burglary.
Corporate and Healthcare
In corporate and healthcare settings, access control plays an elevated role, especially in the age of COVID. There’s a greater need to understand (and sometimes control, such as in the NICU or elder care units) the comings and goings of people and controlling this physical access through technical means (not just through security personnel) becomes crucially important.
Designing an Effective Security System to Reduce Risks
An effective security system, one that’s carefully designed taking a holistic approach to security and safety, is a crucial element in combating whatever physical security and safety risks are present in any physical environment.
But what exactly does it mean for a security system to be holistically and effectively designed, and how can you improve your efforts in doing so?
Here are three strategies to incorporate into your physical security program.
1. Collaborate with Vendors, Integrators, and Partners
Designing truly effective, comprehensive systems requires collaboration at a deep level. No one entity or role has all the tools and information needed to build out the best systems possible. But historically it’s been difficult for various parties (vendors, integrators, partners, and corporate or campus physical security leaders) to communicate clearly with one another and to share resources.
With System Surveyor, there’s a better way.
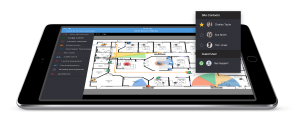
System Surveyor is a collaborative system design platform that empowers all parties to work together in a central cloud location, designing systems in a shared visual space that offers unprecedented insight and clarity. Use the companion mobile tablet when out in the field and synchronize pictures and requirements to the cloud for work with your team.
2. Be Visual and Get More Stakeholders Involved
Part of the difficulty in designing systems well is that everything tends to feel abstract when it’s on paper. Anything you can do to make the process more visual and less pen-and-paper oriented will help to get more involvement from stakeholders. Senior decision-makers may hold the power, but they aren’t as interested in the dry details of what goes into good system design. By making those designs come to life in System Surveyor’s visual platform, you’ll allow more people to understand more quickly what’s going on — increasing both buy-in and collaboration.
3. Do a Proper Budget Estimation, Considering Trade-Offs or Planned Phases
Last, it’s crucial to build a proper budget estimation, one that’s based on real-world information and accounts for all components, accessories and support materials that go into building a system.
Once again, System Surveyor makes this simpler, thanks to its built-in budget estimation tools and its ability to create an automated bill of materials for any project.
You’ll also want to consider necessary trade-offs to stay within budget, or work with planned phases if an all-at-once installation isn’t financially feasible.
See how System Surveyor makes budget estimation simple and shows the risks and benefits of proposed trade-offs in real time, plus 5 advantages of using System Surveyor for budget estimation.
Maintaining a Physical Security System: Managing the Lifecycle of the System

Designing an ideal physical security system is only one part of the equation. Once designed and implemented, there is an ongoing lifecycle that must be managed to ensure that the system stays operational and up to date.
Consider the risks to your campus or business if a portion of your security system goes down and an incident is missed. Loss of property, missing evidence, and increased risk of incidents are all risks of an unmaintained security system.
Of course, systems quickly grow in complexity, especially on larger campuses. Even knowing what devices are in a security system can be a challenge, let alone formulating a plan to keep everyone up to date.
We recommend a monitoring system or service provider to help you to this end. Such a service will proactively reach out with critical information if they notice a component failure or outage, alerting you to the issue before it creates even greater problems for you.
We also highly recommend that organizations keep a digital as-built that shows exactly what is included in the security system. Here, too, System Surveyor is an ideal cloud-based platform: you can create a system of record after major installs (by changing a file to read-only), and you can also maintain a live, editable plan where you can note updates, replacements, expected end of life, and more. Moreover, you can share the as-built (even a dynamic one that considers moves/adds and changes) with public safety, customers, project managers and other stakeholders to act as a coordinated effort to manage the system. Putting everyone on the same page to lower physical security risks is vital.
Try System Surveyor Today
As you work to continually reduce and mitigate physical security and safety systems risks on your organization’s properties and in your facilities, System Surveyor can be a powerful tool—both for collaborative design and for long-term maintenance and record-keeping. It’s a centralized, cloud-based platform that empowers you to collaborate like never before and to maintain a living digital as-built for ongoing maintenance needs.
Ready to see more? Try System Surveyor free today!
