A physical security assessment is a vital process for all organizations concerned with the physical safety of people and property within a building or campus. It’s an assessment of how effective an organization’s physical security measures are, along with a rough guide toward developing a roadmap for future improvements.
This month, we’re diving into why this process is crucial for organizations and institutions of all sizes, how to approach it and some new ways to make it more efficient and effective. With more limited resources, labor and a tight supply chain; every effort to make these assessments more accurate and actionable will be welcome and celebrated at an organization.
What Is a Physical Security Assessment?

A physical security assessment is the first step in determining the state of affairs of the security of a property or campus. It’s an initial step that may include a site survey and is a discovery phase where corporate and campus security leaders and vendors work to determine the following:
- The layout of the building and the security devices and technology that are currently implemented
- The operational state of the equipment
- The gaps that need to be addressed
- The goals an organization has around its upcoming physical security posture and future plans
In short, the physical security assessment gathers all the preliminary information — so that the ongoing physical security implementation and life-cycle as a whole — can succeed.
Conducting a physical security assessment is wise for any organization that is responsible for the people, physical assets, and the security and safety of a building or campus. Educational campuses (K-12 and higher ed), corporate buildings and campuses, governmental facilities, airports, healthcare facilities and entertainment venues are top candidates, as are utilities and critical infrastructure. We’ve written before on the 8 steps to conducting a successful site survey, so be sure to check out that post before you begin.
5 Actionable Tips on How to Conduct a Physical Security Assessment
As you prioritize a physical security assessment for the spaces under your care, you may be wondering what specifically to do. It’s one thing to agree that conducting an assessment is important; it’s another to understand how to conduct a physical security assessment.
Many of the users of our software platform use it to conduct a physical security assessments so that they can determine what technology needs to be refreshed, added or budgeted for in the future. Along the way, we’ve gleaned these five actionable tips that successful organizations use.

1. Visualize and Map the Technology You Already Have in Place
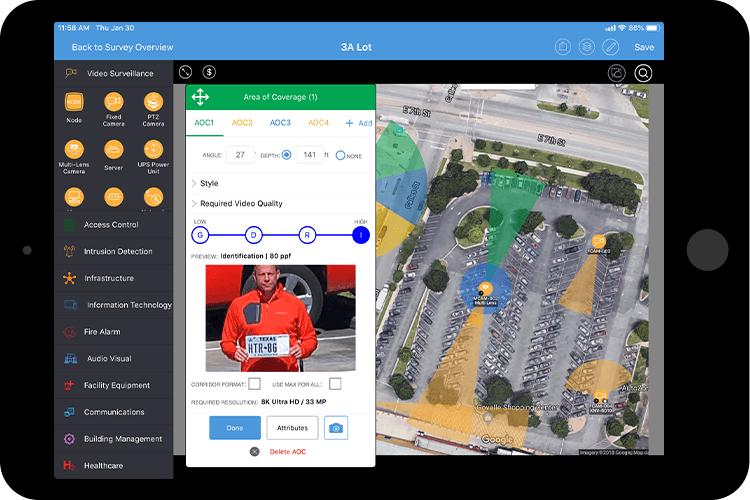
A quality assessment starts with getting an accurate picture of what’s already in place. Using a visualization tool like System Surveyor, you can walk a site survey and map out the technology that’s already installed in your facilities. Identify any gaps within your current system and flag these for addressing during this project. Note that you can use the attribute tag of “In Place” during htat process and when you identify a gap, tag it as “Proposed”. This will help with reporting and visualizing for stakeholders.
Many organizations still rely on pen and paper and Excel files to list or map their current technology assets, but this dated method has numerous issues. One of the biggest is area of coverage: how can your organization accurately notate areas of coverage on a pen and paper mockup or floor plan?
As an example, System Surveyor’s Camera Advisor(TM) shows exactly what kind of range, angle, and field of view all the top camera brands and models achieve and allows you to toggle between different cameras to determine which hardware is right for each gap in coverage.
2. Determine if Existing Technology Is Operational
Next up is to identify the health of your current systems. Which cameras and other equipment are operational? Which aren’t functioning or aren’t running reliably? How old is your current security hardware, and what is the mean-time to failure? Has it been inspected regularly?
Missing a security incident because of failed hardware can be a significant risk — and, in some cases, a liability. Security equipment isn’t designed as a one-time install technology. It has a useful life, and it has maintenance needs.
Keeping track of this kind of information in a spreadsheet (or, worse, in a paper notebook) is terribly time-consuming, constantly out of date, and generally not all that useful.
Software platforms can help here too: you want to build out a living digital as-built, which represents exactly what you have in your system at any given time and is kept up with dynamically, along with installation dates, service dates, and other data. Your goal is to operate proactively rather than reactively, helping you determine what needs assessing, replacement or enhancements and when.
3. Identify What Is Needed to Meet Different Risk Compliance Levels
From a pure security standpoint, every installation ought to have the best, most comprehensive physical security products — but in the real world there are always competing priorities. The main one is budget: often, corporate or campus physical security leaders are trying to make the case for more spend, while the ones that hold the purse strings need better information to support the request.
As you engage in a physical security assessment, consider taking a tiered approach that lines up with varying risk compliance or risk tolerance levels.
This starts with a map of what you have now (which we covered in the previous two points). From there, consider planning out what it would take to reach various risk compliance levels (Tier 1, 2, or 3) — and what each higher level would mean from a budget perspective.
A digital mapping and design platform can help you create multiple “looks” on a single property or campus, and with a built-in budget estimation tool could give you accurate estimates of what each level or look would cost.
Global and local security leaders look very professional and build trust when they have information that is easy to show and tell with their business buyers. Help make the decisions easier and you’ll have more success reaching the risk compliance standards.
4. Go from Security Assessment to Proposed Game Plan
The next step is using that original site survey is to design what you want to implement now and in the future. You’ve laid the foundation, determined where the gaps are, and it is time to look at new technology.
Some teams can do this design themselves and others need help. Either way, make sure that you have your assessments complete and prioritize the areas where you may need a more in-depth site survey or next step in dragging and dropping the icons for the technology needed. A great example is Access Control – as an organization, you may be moving to a favorite brand that has a new innovation. This is the stage of initially planning. A good site survey would have pictures, a lot of notes and details all in one place that will allow for this next stage of applying the right devices, software and cabling needed to make it a reality.
This brings us to our next point, working with your favorite service providers. Rarely can one organization or team do it all.
5. Work with Professionals such as System Integrators and Manufacturers
Next, it’s important not to build your physical security assessment (and your site survey) in isolation. Working with system integrators and vendors that you trust is a great way to make sure you’re taking advantage of the latest developments in physical security technology.
System integrators and manufacturers themselves can leverage new technology to help you assess your needs and formulate a plan that meets those needs and pleases all stakeholders. Best of all, they can help to future-proof your system, pointing you toward new developments like AI-powered security cameras and next-gen access control systems and educating you in how to implement and use those systems.
The key here is to find a way to more effectively collaborate with your vendors and integrators. It is not secure to email them floor plans and it is inefficent to send PDF markups. This is the time to get inter-organization collaboration going with a more powerful, easy to use system design tool and platform.
As your integrators if they have a collaboration tool that allows you all to work together both during the proposal process and after the sale. This is new territory for some of them but it is becoming a common use case. If they are a great service provider, they will bring you into the fold or you can invite them into your collaboration. Make sure to learn more about their Standard Operating Procedures so that you know they can deliver what you have plannned!
See how one organization leveraged partnerships with system integrators and manufacturers to achieve next-level results in this benchmark study.
What Doesn’t Work
We’ve walked through five tips that will help you conduct better, more thorough physical security assessments and how they relate to getting to the next level of security.
Following these steps works. We’ve seen it numerous times with clients across numerous industries. But we’ve also seen approaches that don’t work. Stay away from these approaches
CAD floor plan: While a CAD floor plan is better than no real representation of a building, it’s still highly limiting. There’s no way to place interactive physical security elements onto the floor plan, for one. It may be an accurate representation of the physical structure of the building, but it can’t show you the area of coverage of a particular camera and it doesn’t help you envision what a cohesive physical security system would look like.
Pen and paper or dated tech: Too many organizations still rely on pen and paper for their physical security assessments and site surveys, jotting down notes as they walk through a space and then trying to translate those handwritten notes into actionable data later on. Or they rely on tech tools that are dated, systems that don’t allow for the kind of cloud centered, collaborative work that is already transforming the physical security industry.
One More Thought: A Living Document
One more thought before we wrap up: any assessment needs to be a living or operational document. Some assessments get completed and then stuck in a drawer (or, these days, saved to the network), never to be accessed again. These are nearly worthless because they don’t reflect reality (the inevitable changes that happen over time between major overhauls).
What you do with the assessment is just as important as having one because assessment isn’t a one-and-done task. It’s an ongoing process of improvement.
And any ongoing task needs a live, useable document that stays up to date. It’s up to your organization to decide how frequently to revisit your physical security assessment. Make sure to build this into your yearly calendar so it remains a priority.
Better Physical Security Assessments Require Better Digital Tools

Ultimately, the best way to improve your physical security assessment process is to start using better digital tools for data gathering, collaborative system design, budget estimation, area of coverage measurements, and more.
System Surveyor is a category-defining solution to the needs of corporate and campus security leaders and system integrators. Our collaborative design platform drives trust, enables visibility, and helps you work more efficiently and with less frustration.
The first step toward an easier system design future is a demo of the System Surveyor platform. Ready to see it for yourself? Request a demo today!