In the past few years, access control has been one of the primary physical security systems for commercial organizations of all types and sizes. These systems are an important aspect of business or other organizations, protecting all employees, visitors and property.
The Access Control Market is evolving at a rapid pace. According to Mordor Intelligence, the market, as a whole, was valued at $7.65 billion in 2020 and is expected to reach $11.7 billion by 2026. Technology has been a key part of growth within the industry of access control, advancing systems and creating new levels of security.
System Surveyor’s platform helps with access control system design — which is why we sat down with Brach Bengtzen to learn more about access control systems and the industry as a whole.
Brach Bengtzen is the Director of Marketing at ProdataKey (PDK), a leading provider of mobile-first access control solutions. This month, Brach was gracious to share his passion and wisdom with us as we learn more about access control in commercial settings. The following information is based on our interview and the insights Brach brought to our attention.
 What Is Access Control?
What Is Access Control?
Put simply, access control is the technology that controls door access: who has access to which doorways, and when they do and don’t have that access. It’s a physical security technology that’s equally about preventing unauthorized access and providing access where appropriate.
Traditional door access solutions — physical keys and door locks — have plenty of limitations. Inflexibility is the most prominent: you either have a key or you don’t. But access control can be as granular as an organization needs it to be, controlling access at the individual level, using granular timeframes, and even providing contextual adjustments like first-in rules and lockdown triggers.
Access control systems offer role-based access control via an electronic credential, be it a smart card, a key fob, or even mobile access via a smartphone or mobile app like the Prodatakey app.
Why Is Access Control Important?
Access control primarily serves to protect property and life by lowering security risks and controlling who can access the property (whether that’s commercial property like an office building, a secure room within a building, or a complex environment like a corporate, hospital, or college campus).
Generally, this takes the form of restricting the general public from accessing sensitive information and areas.
But the beauty of access control technology is that business owners and physical security leaders can adapt a modern access system to meet their specific needs — often working in tandem and integrating with third-party systems like video surveillance and a broader security system.
One example that reflects the importance of access control is seen in K-12 education. A look into PDK’s work at a school in Vail, Colorado shows how secure buildings and integration are top priorities with such large campuses. Their mobile-first access control solution allowed campus physical security managers to set up a variety of customized settings and instantly initiate lockdowns and intrusion detection during security events. They’ve even set up automation tied to their gunshot detection system that can initiate a lockdown if the detection system activates. Learn more about the different benefits PDK access control brought to this Colorado school:
What is Cloud-Based Access Control?
To explain cloud-based access control, we first need to back up and talk about the history of the industry. The first access control systems were 100% on-premise: they operated using on-site servers and computer workstations physically connected to the facility’s network.
And while some of the underlying tech has improved, many of the access control systems sold today are still using this on-prem model.
In contrast, cloud-based access control systems don’t rely on on-site hardware support or third-party systems of any kind. They connect directly to a campus or commercial building’s network and, from there, out to the cloud. Instead of being controlled by a single on-site workstation, cloud-based access control systems put control in your hands — no matter where you are.
PDK’s mobile-first approach means an administrator or manager can control the entire access control security solution from a smartphone, tablet, or laptop — from anywhere with a network or cellular connection.
Benefits of Cloud-Based Access Control
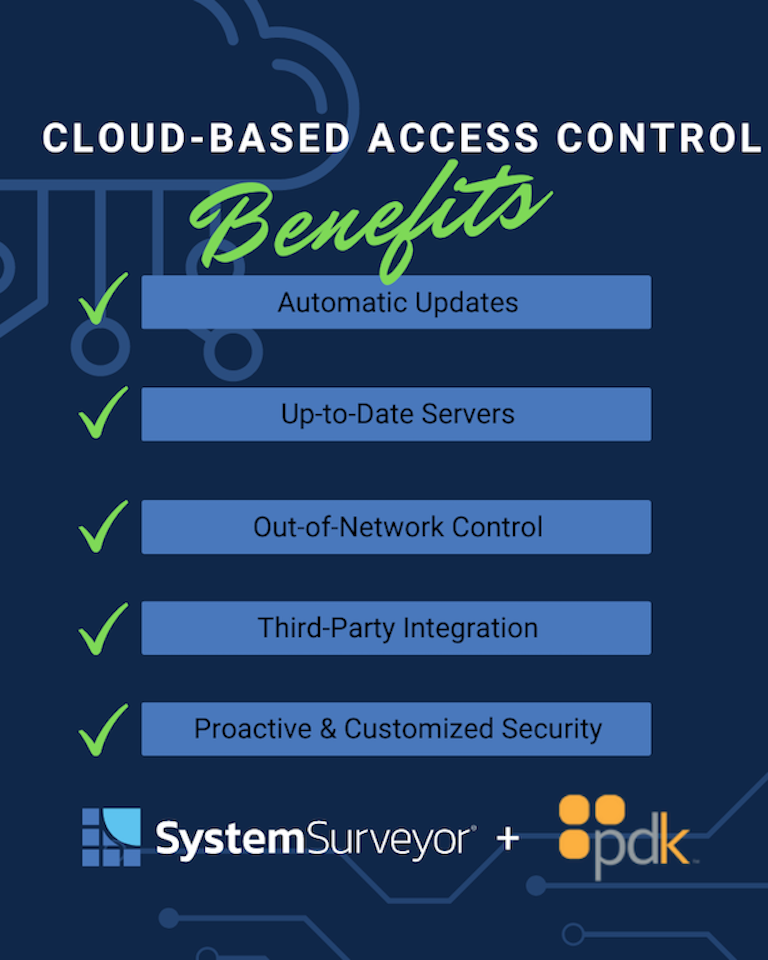
Again, understanding the benefits here starts with knowing the limitations of legacy systems. The legacy on-prem model has numerous vulnerabilities. First on the list is the challenge of updating systems (software and firmware) when exploits are discovered.
Generally speaking, updating on-premises access security systems required (and still requires) a truck roll. Someone has to physically connect to many of the hardware elements to install updates. Since these updates are so time- and labor-intensive, what we see is they just don’t get done promptly, if at all.
With a cloud-based access control system, updates happen automatically: your hardware provider pushes updates out to the cloud, and devices update themselves, often with no human intervention needed.
Along similar lines, many legacy systems are no longer supported at all: their manufacturers have abandoned them or gone out of business. It’s not uncommon to see legacy systems still controlled on a Windows 7 PC—because the software can’t run on any newer versions of Windows. Microsoft stopped supporting Windows 7 years ago, so both the OS and the software controlling the system are deeply vulnerable to exploitation.
Cloud-based systems aren’t tied to a PC or legacy software. They run in the cloud, on servers that are always kept up to date.
Last, the cloud brings much greater proactive security. On-premises systems rely on the strength of your network’s defenses. And, as good as they are, you probably wouldn’t say they’re better than Google or AWS, right? By moving to the cloud, you gain the highest levels of enterprise-grade security.
Access Permissions & User Roles in Access Control
Most access control systems use a tiered system with multiple user roles:
- Administrator: the end-user managers (think security leads, property managers, etc.) with full access. They manage the system and the other people with access to it.
- Managers: a role with limited admin privileges, such as managing a division or single building on campus. Managers can issue credentials and control access to their allotted space without seeing or controlling other managers’ responsibilities.
- Reporter: a role that can only view reports (perhaps a department supervisor).
- Employees, students, and tenants: the “end-user users”; these roles have access credentials assigned to them but cannot access the system itself.
Additionally, the system integrator (the partner that installs and/or maintains the system) often has a super-admin capability with full control over configuration, hardware, and software.
The Future of Access Control
As far as what’s driving innovation in the industry, unfortunately, the primary answer is crime, combined with the overall advance in technology. As technology broadly becomes more powerful and capable, it changes the capabilities of bad actors. The way crimes happen continues to evolve, and so the physical security industry must evolve to face those threats. One example is duplication of credentials. It’s easier than ever to copy basic keycards or key fobs. While electronic credentials are still far more secure than physical keys and traditional locks (because you can revoke access instantly), duplicate credentials are a real concern.
PDK has responded to this threat with the new Red Line. These devices are non-cloneable, giving organizations an extra layer of security and peace of mind.
The market is growing, too: we’re seeing more and more senior care living facilities, multi-tenant residential, 24/7 gyms, and K-12 schools show a need for advanced access control solutions. It also became obvious during the pandemic that the ability to manage access to facilities also needed innovation and upgrade.
As the market expands, so do the needs — and the solutions companies like PDK are developing.
The Reality of Biometrics in Access Control
Biometrics holds a promising future, but the reality isn’t like what you see on TV. Existing solutions aren’t reliable enough to operate on their own. We all saw a version of this with face-based phone unlocks, which were crippled by mask-wearing during the pandemic. Commercial security applications of this technology can fail over even smaller changes, such as growing or getting rid of a beard.
So, with today’s available technology, biometrics don’t work as a standalone solution. And if you have to have a backup or failsafe system, the potential added security of biometrics is impractical anyway.
Tools for Integrators & Security Leaders
Many tools and systems are available to help integrators and security leaders as they plan, design, budget, and implement updated or new technology.
One is the concept of a fully integrated access platform, where multiple security systems are pulled into one centralized control platform. Integrating cloud-based security cameras with access control can be powerful: even from off-site, you could view via smartphone who’s standing at a door requesting access and decide whether to admit that person.
PDK can push its access control to video management software, allowing this kind of control.
Another stellar tool essential for any integrator’s toolkit is System Surveyor.
How System Surveyor Helps Access Control
The collaboration that forms from PDK’s integration with System Surveyor software is a win-win situation: for one, the platform helps dealers understand what a system design looks like. They can build out wiring paths and map out exactly which PDK controllers and readers go where. It’s a great advantage for installation partners and integrators, too: no more getting to an install with not quite everything you need to finish the job!
Within access control, System Surveyor helps make system design more efficient. For example, the System Surveyor app has a cabling tool that can measure cable length against a to-scale building blueprint. It’s easy to identify when a cable run might be too long or too inefficient and pivot to a different controller configuration.
See a recorded webcast talking about how System Surveyor and PDK work together.
Next Steps
The next generation of mobile-first access control is here, and PDK’s security solutions are easier than ever to design and deploy thanks to System Surveyor’s design platform. With System Surveyor, dealers can more easily understand and view system designs, and integrators achieve numerous time-saving efficiencies thanks to our collaborative design platform.
We appreciate Brach taking the time to help us better understand access control and how PDK is innovating mobile-first systems.
To explore PDK’s solutions further, visit their website or contact their sales department at sales@prodatakey.com | 801.317.8802.
And to see how System Surveyor can transform your system design experience, request a demo today.
